Microsoft 365 Integration with Libraesva ESG
To properly integrate Microsoft 365 with Libraesva ESG, you need to configure DNS, relay settings, and connectors for both inbound and outbound mail flow.
Inbound Configuration
- Log in to Microsoft 365 Admin with an administrator account.
- Go to Show all options > Settings > Domains.
- Select your domain and check the MX record.
- The MX record will look like: yourdomain-com.mail.protection.outlook.com.
- Access the Libraesva ESG web console: System > Mail Transport > Relay Configuration > Domain Relay.
- Add or edit your domain and set the Mail Server field to the Microsoft 365 MX record.
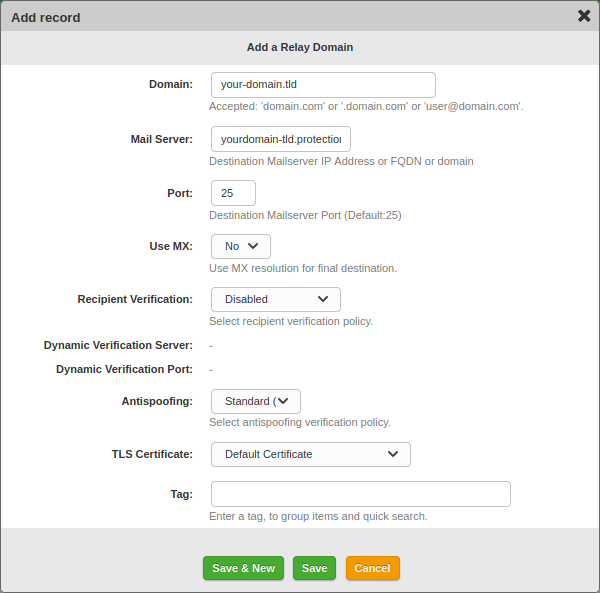
This is the server where Libraesva ESG will forward all inbound email traffic.
Domain Antispoofing
Keep the setting Domain Antispoofing Standard (SPF), unless you are certain no external systems send mail on behalf of your domain.
Disable Microsoft 365 Antispam
Not mandatory, but recommended: disable Microsoft’s internal antispam for emails already scanned by Libraesva ESG to avoid false positives.
- In the Microsoft 365 portal, open Admin Center > Exchange.
- Go to Mail Flow > Rules and create a new rule.
- Assign a name, click More options....
- In Apply this rule if..., select The sender → IP address is....
- Enter the Libraesva ESG IP address.
- In Do the following, choose Set SCL → Bypass spam filtering.
- Save the rule.
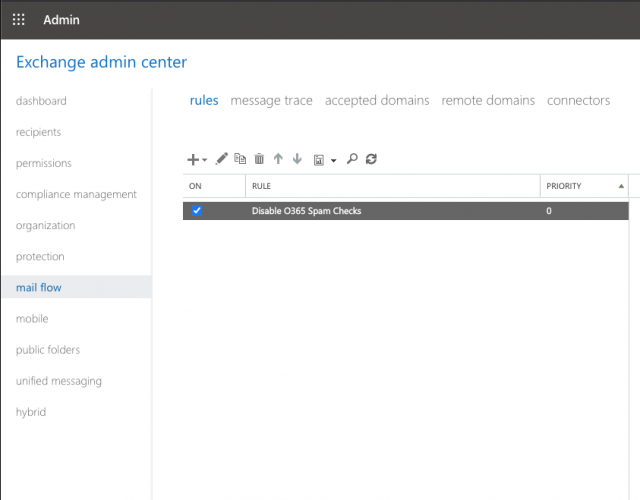
Repeat the configuration under Connection Filtering (direct link).

Configure Inbound Connector
Inbound connectors can be configured in two ways:
- Production: accept mail only from Libraesva ESG (recommended).
- Testing: allow mail also from other sources (not recommended in production).
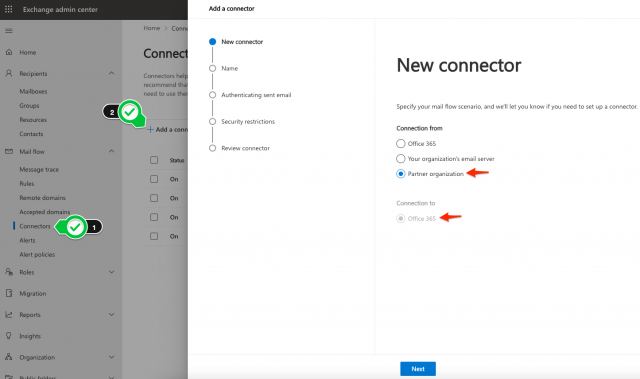
- In Exchange Admin, go to Mail Flow > Connectors.
- Click [+] to create a new connector.
- From: Partner organization → To: Office 365.
- Give the connector a name.
- Use Sender domain: * to include all domains.
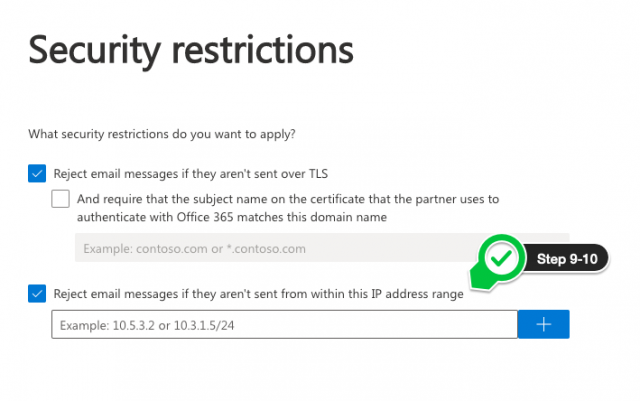
- Select Reject messages not sent from ESG IPs.
- Add the Libraesva ESG IP addresses.
Outbound Configuration
Every new rule or connector may take up to 1 hour to propagate across all Microsoft 365 nodes.
SPF Record
Update the SPF record in your DNS zone to include Libraesva. Always keep spf.protection.outlook.com in the record.
Example SPF record:
v=spf1 mx include:spf.protection.outlook.com include:spf.esvacloud.com -all

